Apple released emergency security updates to fix two zero-days that were used to exploit iPhones and install NSO Group's Pegasus spyware.
The attacks involved malicious PassKit attachments that were sent from attacker iMessage accounts to victims.
The malware can do all sorts of bad things, like steal your data, track your location, and even listen in on your conversations.
If you have an iPhone, you need to update your device right now and activate Lockdown Mode.
Ay y’all, listen up. Apple just released emergency security updates to fix two zero-days that were used to exploit iPhones and install NSO Group's Pegasus spyware. These zero-days are called BLASTPASS, and they're bad news. They allow attackers to infect iPhones without the victim even having to do anything.
The attacks involved malicious PassKit attachments that were sent from attacker iMessage accounts to victims. These attachments are like the ones you get when you add your credit card to Apple Pay. But these attachments are infected with malware.
When the victim opens the attachment, the malware is installed on their iPhone. And once the malware is installed, it can do all sorts of bad things, like steal your data, track your location, and even listen in on your conversations.
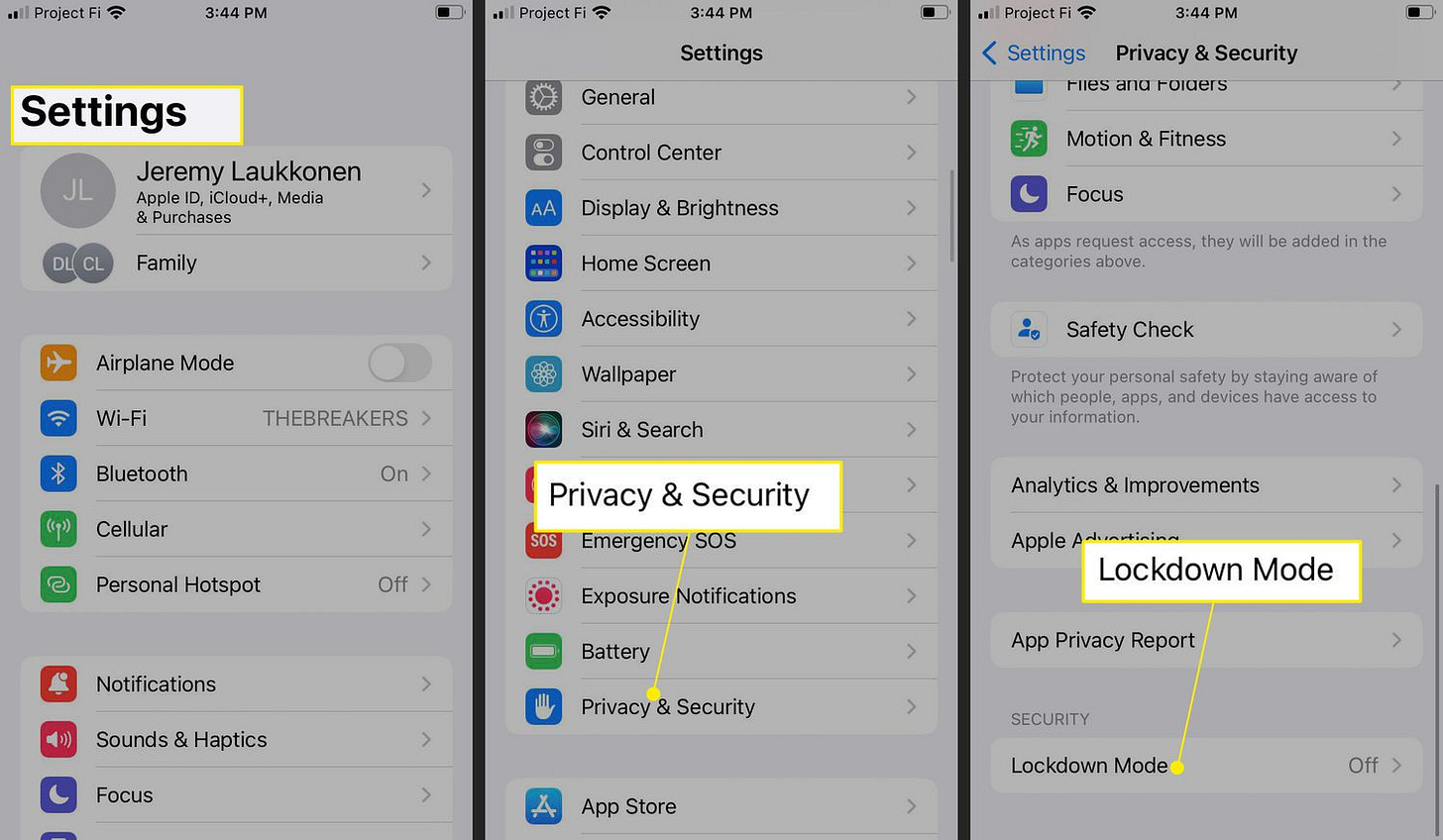
So if you have an iPhone, you need to update your device right now. And if you're at risk of being targeted by a targeted attack, you should activate Lockdown Mode. Lockdown Mode is a new security feature that Apple released last month that blocks a lot of features that attackers could use to exploit your device.
To activate Lockdown Mode, go to Settings > Privacy & Security > Lockdown Mode. And be careful about what attachments you open, especially from people you don't know.
I know this is a lot of information, but it's important to stay safe. So update your devices, activate Lockdown Mode, and be careful about what you open.
Now, I know what you're thinking. You're thinking, 'I don't know anyone who would target me with malware.' But the thing is, you don't have to know someone to be targeted. These attacks are often targeted at people who are working on sensitive information, like journalists or human rights activists.
So even if you don't think you're a target, it's still important to protect yourself. Update your devices, activate Lockdown Mode, and be careful about what you open.
I know it's a lot to remember, but it's worth it to stay safe. So do yourself a favor and update your devices, activate Lockdown Mode, and be careful about what you open.
BLASTPASS TTPs
Targeted individuals: The BLASTPASS exploit was used to target specific individuals, such as journalists, human rights activists, and government officials.
Attack vector: The attack vector was a malicious PassKit attachment that was sent from an attacker iMessage account to the victim.
Vulnerability: The vulnerability exploited by BLASTPASS is a buffer overflow in the Image I/O framework. This vulnerability allows an attacker to execute arbitrary code on the victim's device.
Impact: The impact of BLASTPASS is that the attacker can gain full control of the victim's device. This allows the attacker to steal data, track the victim's location, and even listen in on their conversations.
Mitigation: The BLASTPASS vulnerability has been patched by Apple in iOS 16.6.1, iPadOS 16.6.1, macOS Ventura 13.5.2, and watchOS 9.6.2. Users are advised to update their devices to the latest version of software to mitigate the risk of attack.
Here are some additional details about the BLASTPASS exploit:
The malicious PassKit attachment is disguised as a legitimate attachment, such as a receipt or a boarding pass.
When the victim opens the attachment, the malware is installed on their device.
The malware then communicates with the attacker's command and control server.
The attacker can then use the malware to control the victim's device.
The BLASTPASS exploit is a serious threat to the security of iPhones and iPads. Users are advised to update their devices to the latest version of software and to be careful about what attachments they open.
Pegasus spyware TTPs
Targeted individuals: Pegasus spyware is typically used to target specific individuals, such as journalists, human rights activists, and government officials.
Attack vectors: Pegasus spyware can be delivered through a variety of attack vectors, including:
Phishing emails: The attacker sends a phishing email that contains a malicious link or attachment. When the victim clicks on the link or opens the attachment, the malware is installed on their device.
Watering holes: The attacker compromises a legitimate website and injects the malware into the website's code. When the victim visits the website, the malware is installed on their device.
Supply chain attacks: The attacker compromises a software vendor and injects the malware into the vendor's software. When the victim installs the software, the malware is installed on their device.
Vulnerability: Pegasus spyware exploits a variety of vulnerabilities in mobile operating systems and messaging apps. These vulnerabilities allow the malware to gain root access to the victim's device.
Impact: Pegasus spyware can be used to do a variety of things, including:
Steal data: Pegasus spyware can steal data from the victim's device, such as their contacts, messages, photos, and browsing history.
Track the victim's location: Pegasus spyware can track the victim's location using their phone's GPS or cellular data.
Listen in on the victim's conversations: Pegasus spyware can listen in on the victim's conversations using their phone's microphone.
Mitigation: There are a number of things that can be done to mitigate the risk of infection by Pegasus spyware, including:
Keeping your devices up to date with the latest security patches.
Being careful about what links you click on and what attachments you open.
Using a security solution that can detect and block malware.
Pegasus spyware is a serious threat to the security of mobile devices. Users are advised to take steps to mitigate the risk of infection.